Instructions
Objective
Write a program to create logfile security system in python language.
Requirements and Specifications
This week you will play the role of a security professional whose company believes you are undergoing some Web attacks. The system potentially under attack does a good job of logging all Web requests in which you can pull out potential attacks and save them in a persistent file for your team to review later. The log files you will be parsing are from ModSecurity, which is a free open source Web Application Firewall (WAF) that performs real-time HTTP traffic monitoring.
Your programming assignment will be to first take as an argument the name of a log file. You will then open that log file as text and read through all lines of the file. In ModSecurity Audit log files, lines that contain the string "-B--" are lines containing the request headers. Whenever you see the "-B--" on a line, the next line will contain the GET, POST, etc. request along with the URL. You will look at the line after the "-B--" lines in the file and whenever you see a potentially malicious request, you will insert the line into the database. For looping through the content read from a file you can use something like "next()" or the combination of "readlines()" to read the content of the file and "pop(0)" to get the item from the resulting list. From there you will check if the request line contains some text signifying an attack is being attempted, and if you find that it is, insert the line into your database. Let's look at an example of using readlines() and pop(0) to help speed things up for you:
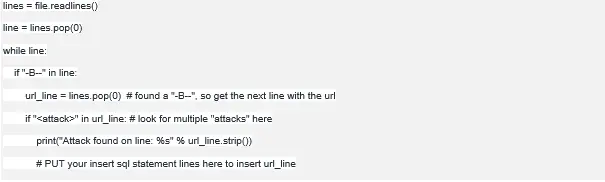
As you are graduate level security professionals I will leave the types of attacks you extract up to you. Again, for every line after a "-B--" line that contains a potential attack in a GET/POST/OTHER request, you will insert the entire line of that log message as a record into your database. You will be graded on how well you were able to pull different types of attacks from the URL lines. Aim for finding at least two different types of attacks in the example modsecurity audit logs provided below.
The first thing your program will need to do is create the database table in a ".db" file. The schema for your table will be simple and will look like:
CREATE TABLE attacks(id INTEGER PRIMARY KEY, attack_line TEXT NOT NULL)
You only need to create the table if it doesn't already exist. Look into the SQL commands pages on how you can tell SQL to only create a table if it doesn't exist.
- modsec_audit.log Download modsec_audit.log
- modsec_audit.log.1 Download modsec_audit.log.1
- modsec_audit.log.2
Source Code
import sqlite3
if __name__ == '__main__':
# Define the attack keywords
attack_keywords = ["GET", "TRACE", "PUT", "POST"]
# First, create the DB
conn = sqlite3.connect('attacks.db')
c = conn.cursor()
# Create the Tables
c.execute('''
CREATE TABLE IF NOT EXISTS attacks
([id] INTEGER PRIMARY KEY AUTOINCREMENT,
[attack_line] TEXT NOT NULL)
''')
# Now, read the file
file_name = 'modsec_audit.log'
counter = 0 # Variable to count the number of attacks inserted into the database
with open(file_name, 'r') as file:
lines = file.readlines()
while len(lines) > 0:
line = lines.pop(0)
if "-B--" in line:
url_line = lines.pop(0)
# Check if the url_line contains an attakc keyword
for keyword in attack_keywords:
if keyword in url_line:
# Insert this url_line into the database
query = f"INSERT INTO attacks (attack_line) VALUES ('{url_line}');"
#print(query)
c.execute(query)
conn.commit()
counter += 1
break
conn.close()
print(f"{counter} attacks have been detected from file {file_name} and stored in the database.")
Related Samples
Explore our curated selection of free Python assignment samples, crafted to aid your learning experience. These samples provide clear solutions and practical insights, assisting you in mastering Python programming concepts with ease.
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
Python
.webp)